Deployment Topology
Buttonwood strongly recommends deploying the Broker within the trusted network where there is no firewall restricting traffic between the Broker and other internal network services such as
DNS, AD/LDAP, NTP, and management clients.
The following diagram depicts a typical deployment of the Broker with network ports listed.
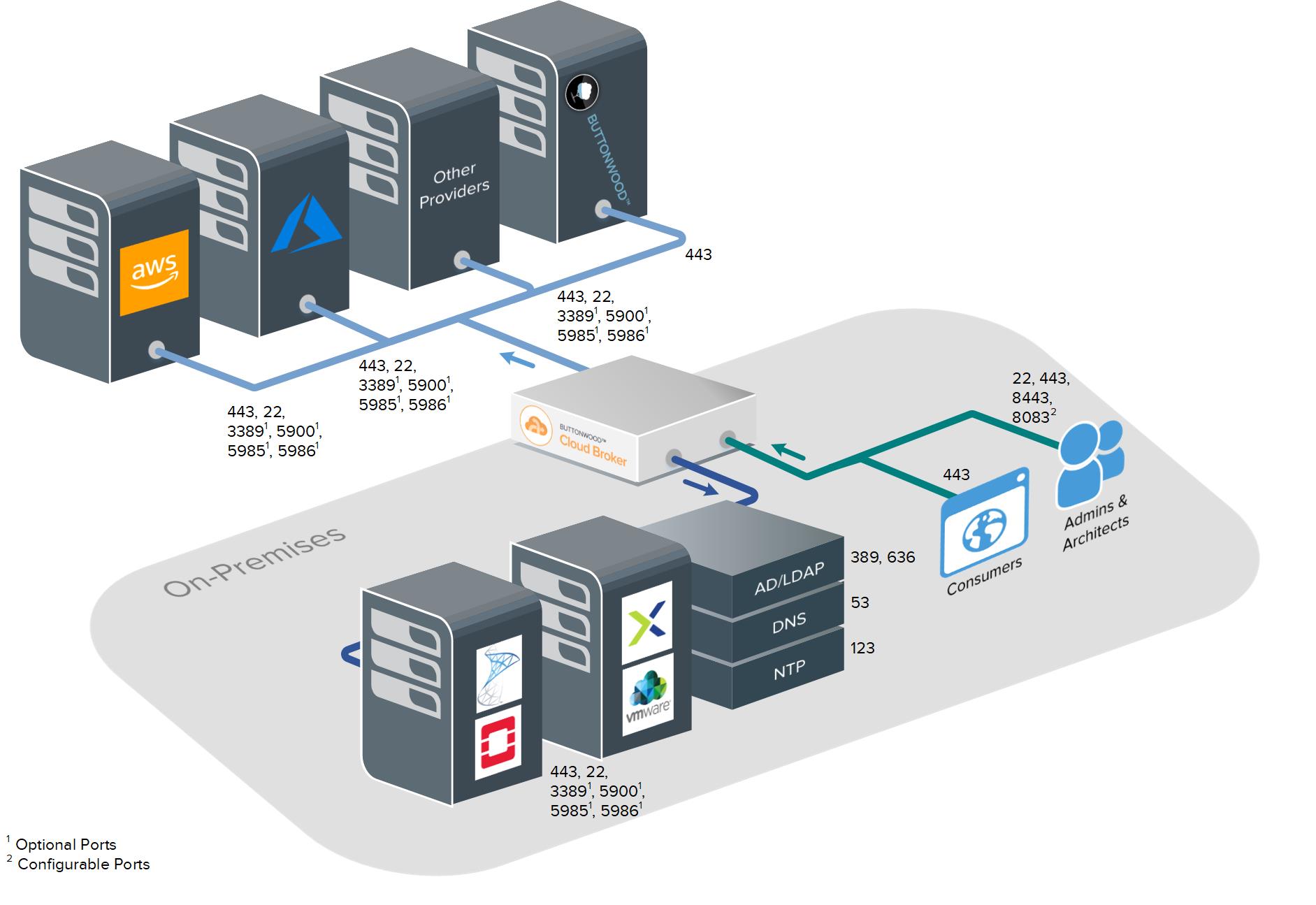
The Broker primarily communicates with external network resources, such as Buttonwood Exchange Services, Cloud Service Provider management endpoints, and software repositories, using outbound HTTPS (TCP 443). This is commonly already allowed in a typical corporate network either transparently or via a network proxy.
Firewall Ports Listing
The following lists the firewall ports which are required to be configured for the Broker appliance to performs its functions.
Broker plugins may require their own specific firewall ports configured. Refer to the plugin documentation on the Plugin Integration Guide.
Inbound Ports
| Port | Protocol | Source | Destination | Additional Information |
| 22 | TCP | Broker Admins |
Broker Appliance |
SSH Required for accessing the Broker management console |
| 443 | TCP | Broker Consumers |
Broker Appliance |
HTTPS Required for access to the Broker Management Web UI |
| 8083 (Configurable) |
TCP | Broker Consumers |
Broker Appliance |
HTTPS |
| 8443 | TCP | Broker Admins |
Broker Appliance |
HTTPS Required for access to the Broker Admin Console UI |
Outbound Ports
| Port | Protocol | Source | Destination | Additional Information |
| 22 | TCP | Broker Appliance |
Deployed Workloads |
SSH Required for management activities carried out on deployed workloads |
| 53 | TCP/UDP | Broker Appliance |
DNS Servers |
DNS Required for internal and external name resolution |
| 123 | TCP/UDP | Broker Appliance |
NTP Servers |
NTP |
|
389, 636, 3269 |
TCP | Broker Appliance |
LDAP Servers |
LDAP (Optional) |
| 443 | TCP | Broker Appliance |
Internet |
HTTPS |
| 3389 | TCP | Broker Appliance |
Deployed Workloads (Windows Instances) |
RDP (Optional) Required by system administrators for GUI based management of deployed workloads |
| 5985 | TCP | Broker Appliance |
Deployed Workloads |
WinRM over HTTP (Optional) Required for management activities carried out on deployed workloads |
| 5986 | TCP | Broker Appliance |
Deployed Workloads |
WinRM over HTTPS (Optional) Required for management activities carried out on deployed workloads |
Management Endpoint URLs
The following lists the management URLs which are used by the Broker when communicating with cloud service providers. These may be used as a reference when configuring whitelists, for example, in proxy server configurations.
Please refer to the article Configuring a Network Proxy if this configuration is required to allow the Broker to communicate to external service provider endpoints.
| Provider | URLs | Description |
| Buttonwood | https://*.bcx.buttonwood.net |
Buttonwood web services operate under subdomains of the bcx.buttonwood.net domain. It is advised to whitelist the entire *.bcx.buttonwood.net domain. |
| AWS | https://*.amazonaws.com |
Amazon utilises a different set of URLs for each service, and in most cases also offer region specific endpoints to reduce latency of requests. The format of the endpoint URL is generally in the format: Where possible, it is advised to whitelist the entire *.amazonaws.com domain. Amazon provides a list of all their endpoints in the following article: https://docs.aws.amazon.com/general/latest/gr/rande.html |
| Azure |
https://*.azure.com
|
Microsoft utilises a number of different inter-operating URLs for their services. Where possible, it is advised to whitelist each service domain. Microsoft does not provide a central location which lists all their endpoints. Some examples of these URLs are as follows:
|