This article provides the steps required to view and manage resources.
Resources include all objects which make up a deployment such as virtual machines, load balancers, SQL servers, etc. It also includes backing services such as security groups, disk volumes, key pairs, etc.
Resources are the children object of deployments, so users require access to deployments to access their resources.
Accessing Resources
This section describes the steps required to access Resources.
Administrative Users should jump ahead to the next step Accessing Resources (Administrative Users).
Prerequisites
- User owns deployments
and/or - User has been assigned permissions to manage deployments
Procedure Steps
- Login in the the Broker UI
- Access the Deployment for which Resources is to be managed
- Select the Details tab
Locate the the Resources and Other Resources sections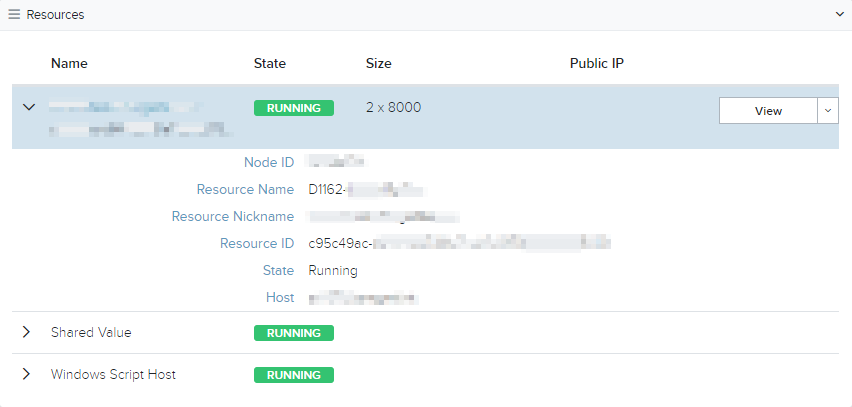
- Click the Resource name or the View button to view details of the Resource
Accessing Resources (Administrative Users)
This section describes the steps required to access Resource as an administrative user.
Non-administrative users should refer to the previous step Accessing Resources.
Prerequisites
- Administrative access to the Broker UI
Procedure Steps
- Login in the the Broker UI as an administrative user
- Access the Deployment for which Resources is to be managed
- Select the Details tab
Locate the the Resources and Other Resources sections
- Click the Resource name or the View button to view details of the Resource
Resource Summary
The Summary screen displays the Resource properties.
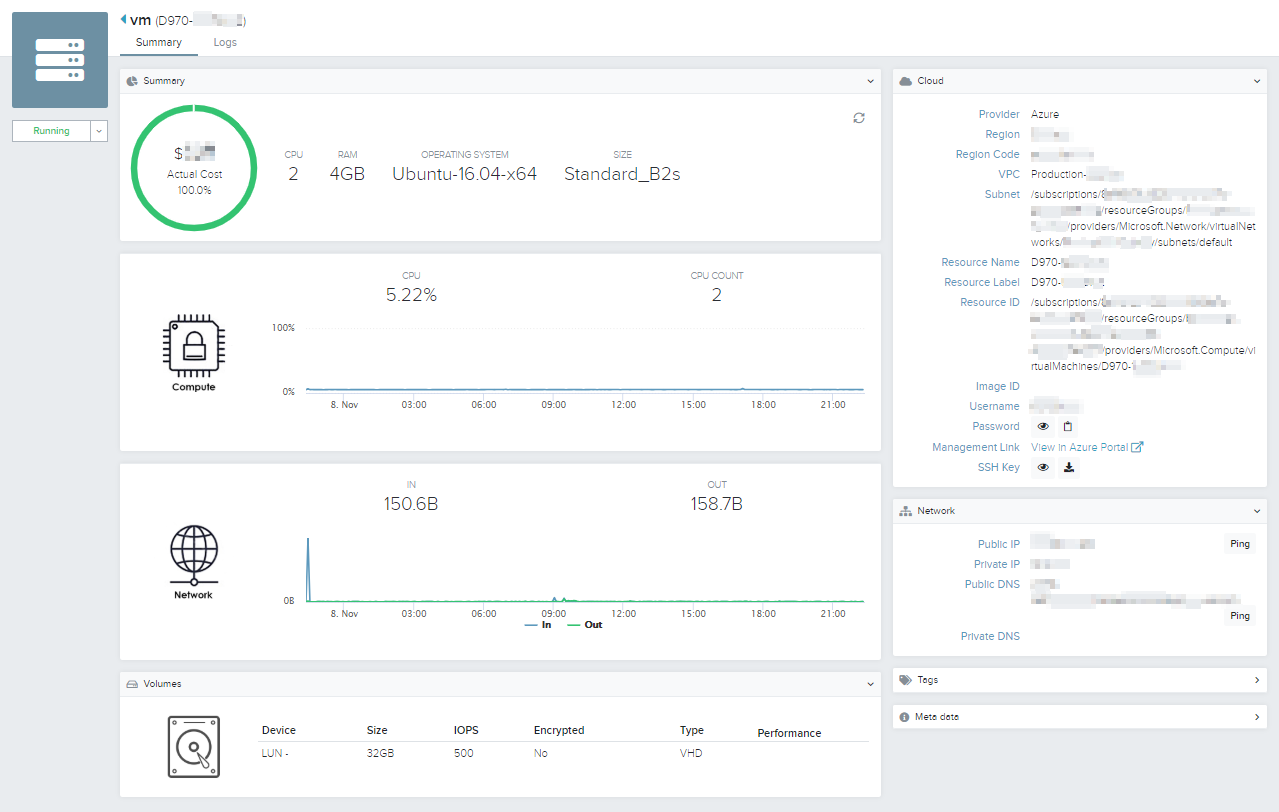
Summary
This section provides a summary of the resource type and cost. Where the service provider supports it, utilisation metrics for compute and network is also displayed.
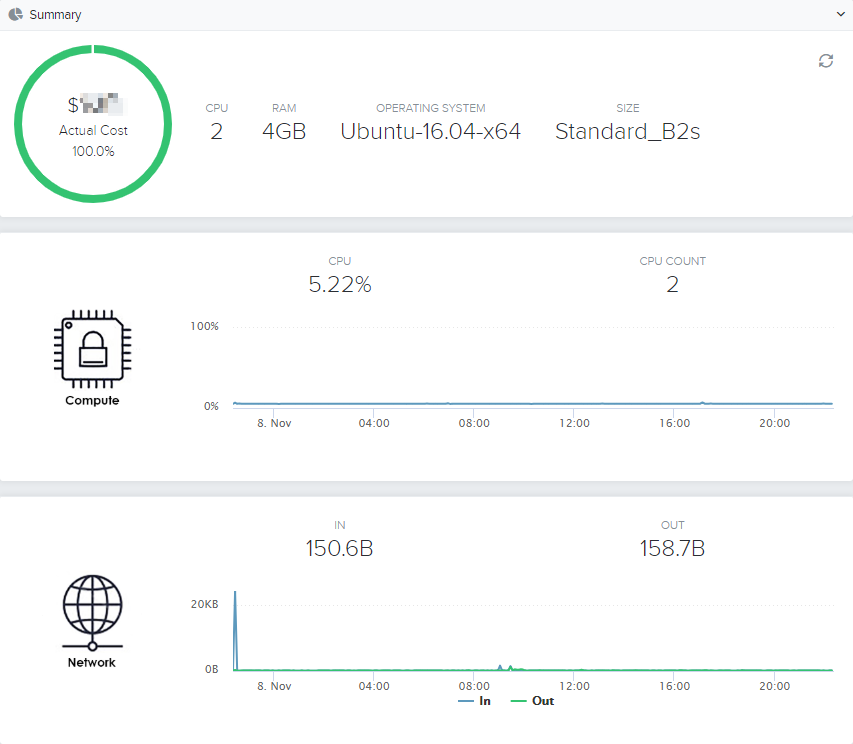
Hover over the graph to view point-in-time metrics.
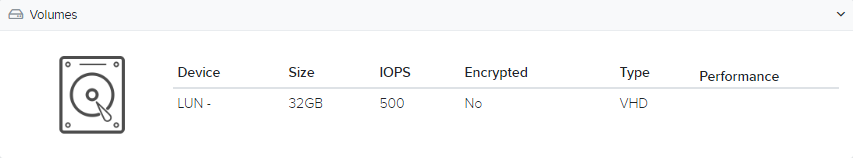
Volumes
This section lists the disk volumes attached to the resource.
Cloud
This section lists the resource's service provider properties.
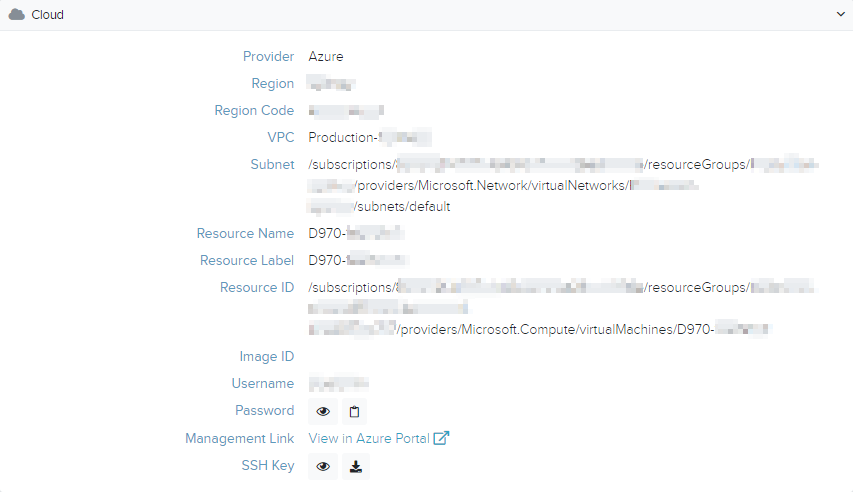
It also provides a deep link to the service provider's management portal in case direct management is required.
Resource owners and Broker administrators can also perform the following tasks:
- View the credentials used to connect to the remote console of the resource
- View and download the private key file to connect to the resource
Network
This section provides the internal and external IP and DNS names for the resource.
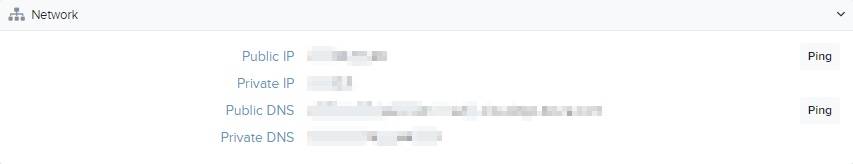
Resource owners and Broker administrators can also perform the following tasks:
- Initiate a network ping test the network endpoints - the tests run for approximately 30 seconds
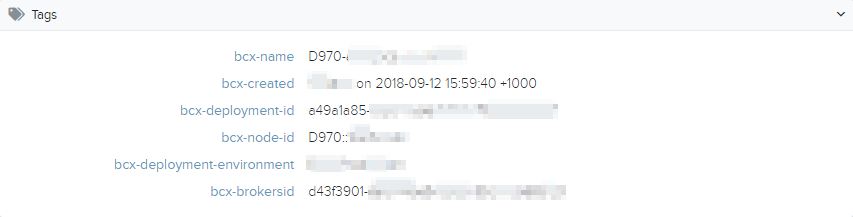
Tags
This section lists the tags assigned to the resource during deployment.
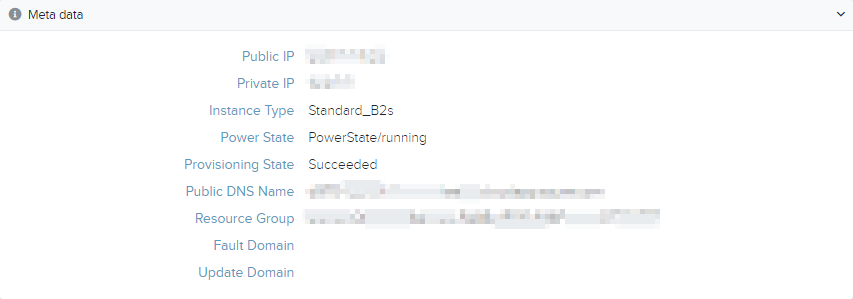
Metadata
This section lists the metadata generated for the resource during deployment.
Resource Logs
The Logs tab displays logged historical events for the selected Resource.

Resource Operations
Some resources also allow management operations to be performed against them, referred to as Day Two Operations - eg. power operations or creating a disk/volume snapshot. These actions appear as a drop down menu when viewing a resource, or against a resource when viewed in the Resources or Other Resources sections when viewing a deployment.
Generic Operations
The following table lists the operations available for all resources.
| Function | Description |
| Edit Nickname | Edits the friendly name of the resource |
| View/Add Tag | Manage tags and tags values, where supported by the service provider |
Type Specific Operations
The following table lists the operations available for each resource type.
| Resource Type | Function | Description |
| Virtual Machine | Power On/Off | Powers on or off the virtual machine instance |
| Reboot | Reboots the virtual machine instance | |
| Resize |
Changes the instance type or compute/memory configuration of the virtual machine Note: At the selected time, this action will automatically power off and power on the virtual machine instance for the change to take effect |
|
| Update Credentials | Updates the stored credentials which are used to connect to manage the virtual machine | |
| Connect | Connects to the console of the virtual machine. eg. RDP for Windows, SSH for Linux | |
| Root Disk | Snapshots | View and create volume snapshots |
| Security Group | Manage | Configure security group rules |