Secret Providers enables rules-based definitions for using external services to store secrets such as passwords and keys.
Using Secret Providers, administrators can ensure that their secrets are securely stored in a service which is relevant to each environment. Secrets exist when configuring Credentials and are also automatically generated when resources are deployed.
The following secret management services are currently supported:
- Local Secret Store (Default, built-in secret provider)
- AWS Secret Manager
- Azure Key Vault
Once Secret Providers have been added, scope rules are created to define conditions for where auto-generated secrets are stored. For example, when a virtual machine is deployed to a service provider, a SSH key is automatically generated to enable access to the deployed virtual machine. This SSH key is stored within a Secret Provider as resolved by the created set of Scope Rules.
This article describes the steps required to manage Secret Providers and their scope rules.
Prerequisites
- Administrative access to the Automation UI
- Access details for the relevant secret manager service
Adding a Secret Provider
This section describes the steps required to add a new Secret Provider.
The steps are provided are for an AWS Secret Manager service, but are generally identical for other secret manager services.
- Log into the Broker UI as an administrative user
- Navigate to Admin > Control Panel
- Select the Secret Providers tile

- A list of existing Secret Providers is displayed
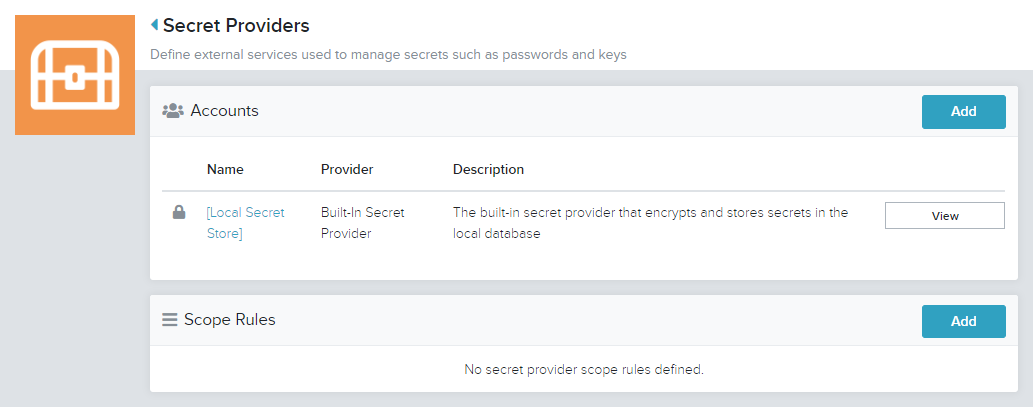
- In the Accounts section, click Add
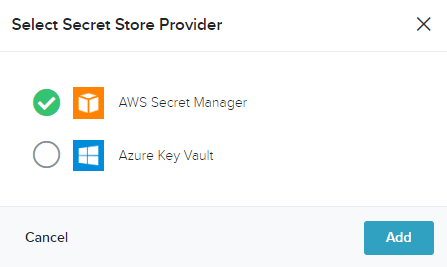
- Select a supported external service to add
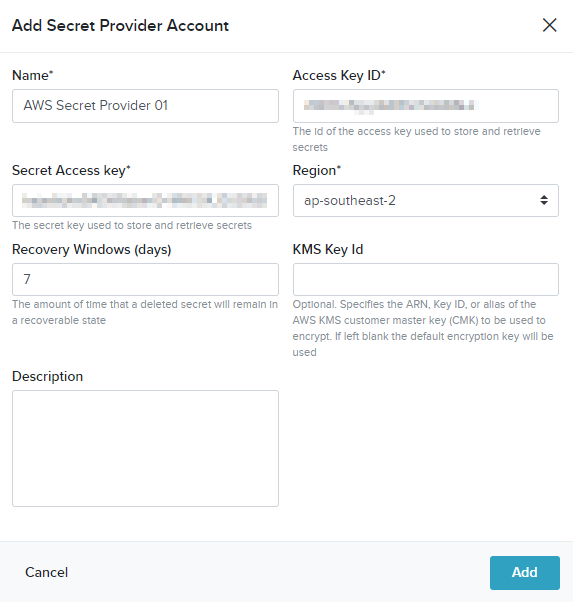
- On the Add Secret Provider Account screen, provide the following information:
- Name: A friendly name for the defined service
- Access Details: The relevant details to access the defined service
Note: These will differ across supported external services - Description: A description for the defined service
- Click Add
- The Secret Provider has been added
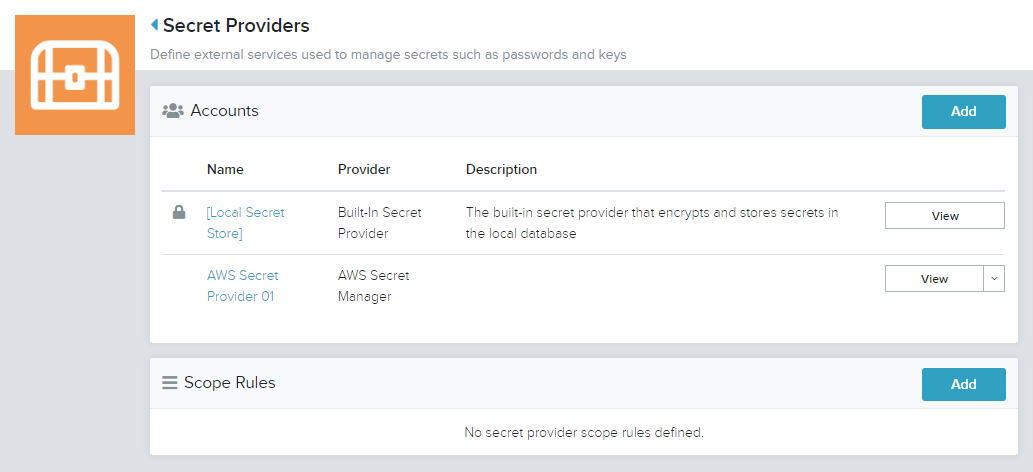
Removing a Secret Provider
This section describes the steps required to remove a Script Host.
- Log into the Broker UI as an administrative user
- Navigate to Admin > Control Panel

- Select the Secret Providers tile

- A list of existing Secret Providers is displayed

- On the Secret Provider to be removed, select the Edit drop down list
Click Remove
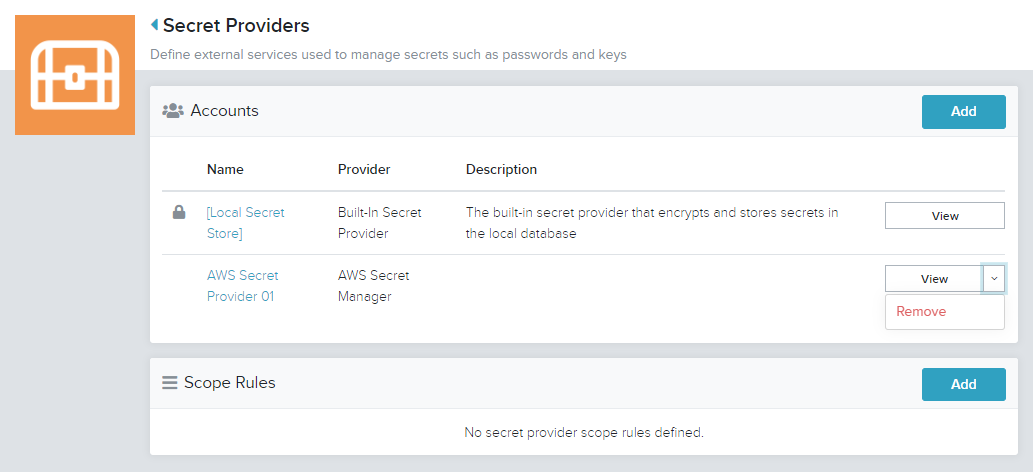
- Click Remove
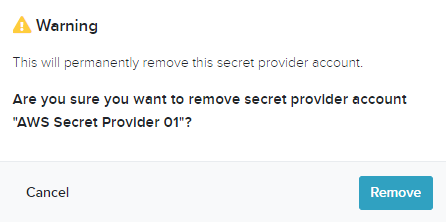
- The Secret Provider has been removed

Creating Scope Rules
This section describes the steps required to manage Scope Rules.
- Log into the Broker UI as an administrative user
- Navigate to Admin > Control Panel

- Select the Secret Providers tile

- A list of existing Secret Providers and Scope Rules is displayed

- In the Scope Rules section, click Add
- On the Add Secret Scope Rule screen, provide a name for the rule
- On the Add Secret Scope Rule - Scope screen, provide the following information:
- Environment: The environment when this host will be used
- Account/Network: The cloud account or specific network when this host will be used
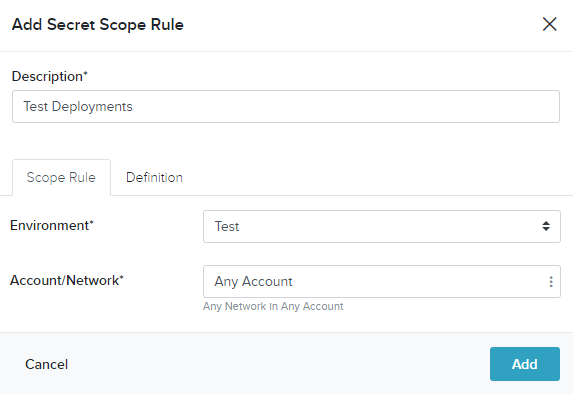
- On the Add Secret Scope Rule - Definition screen, provide the following information:
- Secret Provider Account: The Secret Provider to use for this rule
Note: This list is generated from the list of created Secret Provider accounts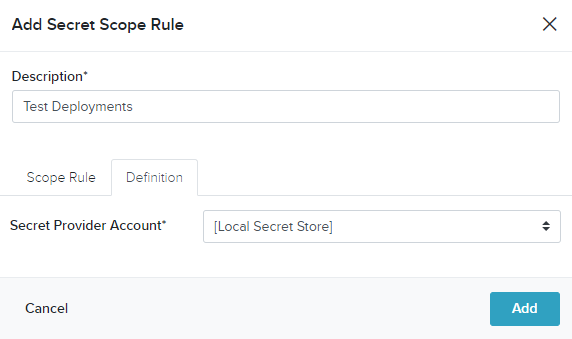
- Secret Provider Account: The Secret Provider to use for this rule
- Click Add
- The Scope Rule has been added
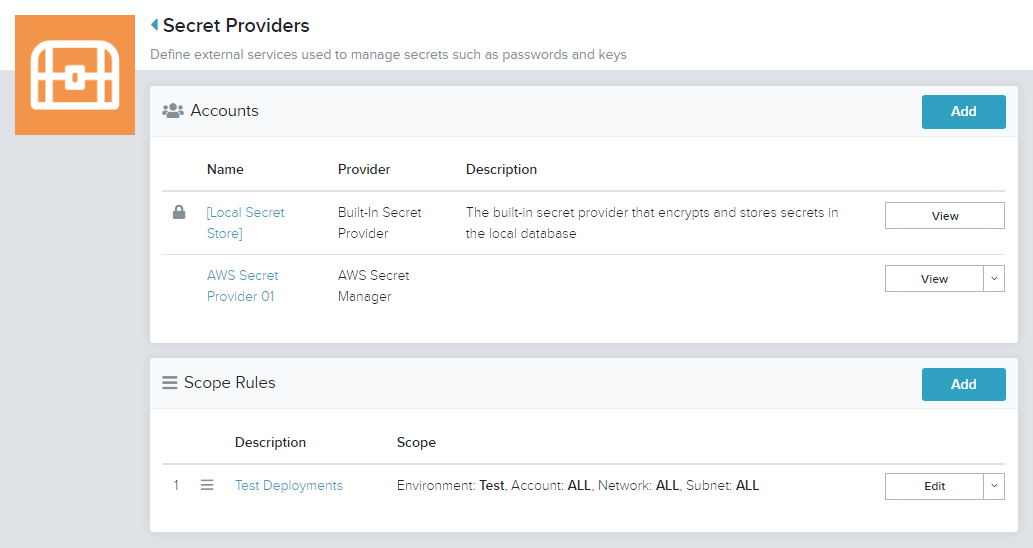
- Additional rules can defined and ordered - if multiple rules are defined, they are evaluated and matched in a top-to-bottom order

Note: This example defines that any deployments to the Test environment will have their secrets stored in the Local Secret Store, and any deployments to the Production environment will have their secrets stored in AWS Secret Provider 01.